
Do you have the right security services for your business?
MTN is a company specialized in the integration of security systems, ranging from video surveillance and access control

Perimeter network security is a crucial aspect of protecting an organization’s systems and data. A perimeter network risk assessment allows you to identify potential vulnerabilities and threats, and develop an appropriate security plan to mitigate the risks. In this article, we’ll explore the steps required to perform a perimeter network risk assessment and come up with an effective security plan.
In today’s digital environment, organizations face increasingly sophisticated threats seeking to exploit vulnerabilities in their networks. A well-protected perimeter network is essential to prevent attacks and ensure the integrity of systems.
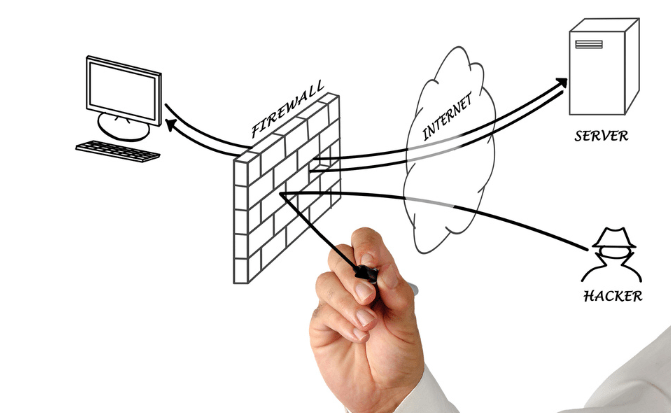
Performing a risk assessment of your perimeter network is critical for several reasons. First of all, it makes it possible to identify the possible vulnerabilities and threats to which a perimeter network is exposed. This helps to understand potential risks and take preventive measures to mitigate them.
In addition, a risk assessment of the perimeter network helps to establish priorities in terms of security. By understanding the most critical risks, organizations can allocate adequate resources and efforts to protect their systems and data.
The frequency with which a perimeter network risk assessment should be performed can vary depending on the size and nature of the organization. However, it is advisable to carry out periodic evaluations, at least once a year, or after significant changes in the network infrastructure.
Performing regular assessments is critical to ensuring the ongoing security of your perimeter network. As cyber threats evolve and become more sophisticated, it is important to constantly evaluate and update existing security measures.
In addition, changes to the network infrastructure, such as the implementation of new technologies, the addition of servers, or the expansion of the network, can introduce new risks and vulnerabilities. Therefore, it is crucial to perform risk assessments after these changes to identify any security gaps and take the necessary steps to mitigate the risks.
Performing a perimeter network risk assessment involves several essential steps. Here are the main ones:
Conducting a perimeter network risk assessment and developing an appropriate security plan are critical steps in ensuring the protection of an organization’s systems and data. By identifying and mitigating risks, organizations can strengthen their security posture and reduce the likelihood of security incidents.
At MTN Services we have technological solutions to help you convert your company to digital transformation in Paso, TX

MTN is a company specialized in the integration of security systems, ranging from video surveillance and access control

FLIR cameras use thermal imaging technology to capture infrared radiation emitted by objects and convert it into visible images.

In today’s business world, security and control are fundamental aspects to guarantee the proper functioning of an organization.